On July 1st 2018, a new devastating policy flushed out to all Ugandan based internet users. While VPNs received massive downloads for the next weeks of July. Only a few users still oppose the policy with many trashing blocked services for open versions and a majority opting to pay the UGX 200 bount that recently tunneled into UGX 4.4bn for URA.
Among the key reasons why you must not fully rely on VPNs is your privacy, which is the crystal at stake checks with threats affiliated to the tunnels created in the whole process. Henceforth, attackers can decide to set up free VPNs in the Google or Apple store and collect free information from bypassers. By the same fashion, these are some of the risks you will have to battle with whenever you power on your VPN.
Unruly Privacy tweaks
Back then the core reason of having a VPN installed was maximum privacy generated through a secure tunnel to authorized offices. However, each time you switch on that VPN, you are granting easy access to your privacy which can be manipulated in any way even with the https flag turned on.
Imagine if a stranger knew all about you and a full dictionary of all your phone contacts? This is the exact situation fed to VPNs since the team of developers didn’t build their software for charity, But instead, a pool to fetch some valuable digits. Henceforth, by turning on that VPN switch or even having it on
Phishing attacks
Phishing which sounds more like the fresh waters activity is one of the dangerous acts that you can never wish to see visiting your computer or smartphone. Through Keyloggers and secret lines of code embedded in multiple VPN apps/ software, an attacker on the other side can easily see each and every button producing beeps on your computer. In addition, your passwords and usernames from websites visited are received as background tasks in a plain format making you vulnerable to illegal posts/messages sent out on your behalf.
Imagine if your bank has an internet banking option and you seem to be a loyal fan over the ordinary USSD version. Each time, you type in the bank secret Login credentials, a broke attacker on the other side of the system watches each and every node of your account to later tease your account with a single standalone figure.
Your data served to hackers at no cost
Unlike Phishing which involves a dish of your information sent out to a waiting black hat client for free. Serving your data to strangers is beyond phishing and privacy tweaks to your device. Just like many new security loopholes are discovered every now and then, VPNs, on the other hand, are free to download but can easily fetch each and every node of your personal data in realtime since everything you do flows directly through the developer servers.
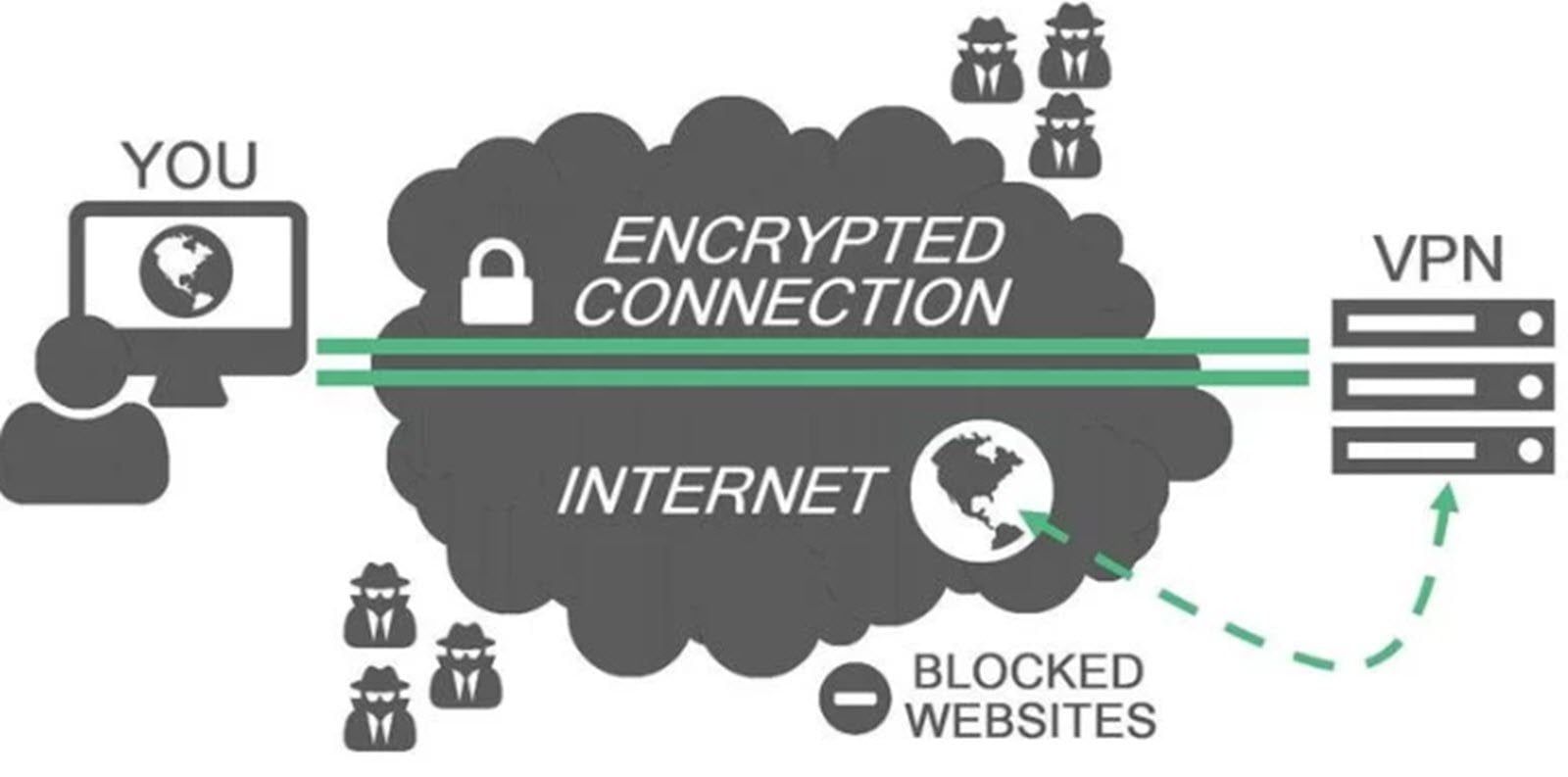
In a glimpse of an eye, servers hosting your virtual VPN address have access all corners of accepted permissions on installation. Well, you could already be a victim of this but you can change that by either abiding to the Government’s OTT tax rule or else create a custom VPN at your home or workplace. More so, you could as well search for trusted paid VPN services available on the internet and smartphone stores with price actions trembling for as low as $1 approx UGX 3700.

