A major vulnerability has been discovered in WhatsApp messaging app and hackers can use it to inject commercial spyware onto Android and iOS phones by simply calling the target. According to the The Financial Times, the spyware was developed by Israel’s secretive NSO group, and can be installed without trace and without the target answering the call including users in Uganda among many other countries. The details were confirmed by the security researchers and confirmed by WhatsApp.
The effect of this spyware is that it will turn on a phone’s camera and mic, scan emails and messages, and collect the user’s location data. To protect yourself, we highly recommend for you to update the app immediately to close the security hole.
“WhatsApp encourages people to upgrade to the latest version of our app, as well as keep their mobile operating system up to date, to protect against potential targeted exploits designed to compromise information stored on mobile devices,” said WhatsApp in a statement.
The vulnerability discovered in early May, was targeted as recently as Sunday when a UK-based human rights lawyer was attacked by NSO’s flagship Pegasus program, according to researchers at Citizens Lab. The attack was blocked by WhatsApp. WhatsApp is investigating the situation but is so far unable to estimate the number of phones successfully targeted by the exploit, said a source speaking to the FT.
“This attack has all the hallmarks of a private company known to work with governments to deliver spyware that reportedly takes over the functions of mobile phone operating systems,” said WhatsApp in a statement provided to The Financial Times. “We have briefed a number of human rights organizations to share the information we can, and to work with them to notify civil society.”
Is govt spying on citizens?
NSO says it sells Pegasus to governments and law enforcement agencies to help fight terrorism and crime. But that hasn’t stopped the company’s spyware from being used by countries, organizations, and individuals undeterred by human rights concerns.
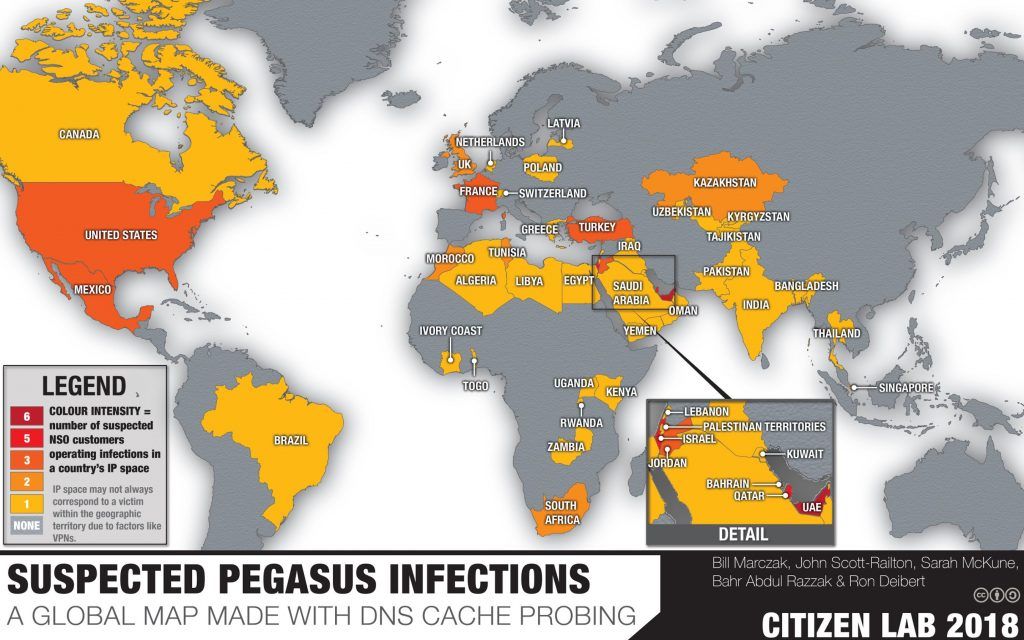
Researchers claim that NSO’s powerful spyware has been used by as many as 45 countries to aid in the persecution of dissidents, journalists, and other innocent civilians. In Uganda, the software has mainly been used on MTN network according to the research where it was part of the suspected NSO Pegasus infections associated with 33 of the 36 Pegasus operators they identified in 45 countries. Other countries in Africa include ; Kenya, Togo, South Africa, Algeria, Cote d’Ivoire, France, Morocco, Tunisia, Rwanda and Zambia.
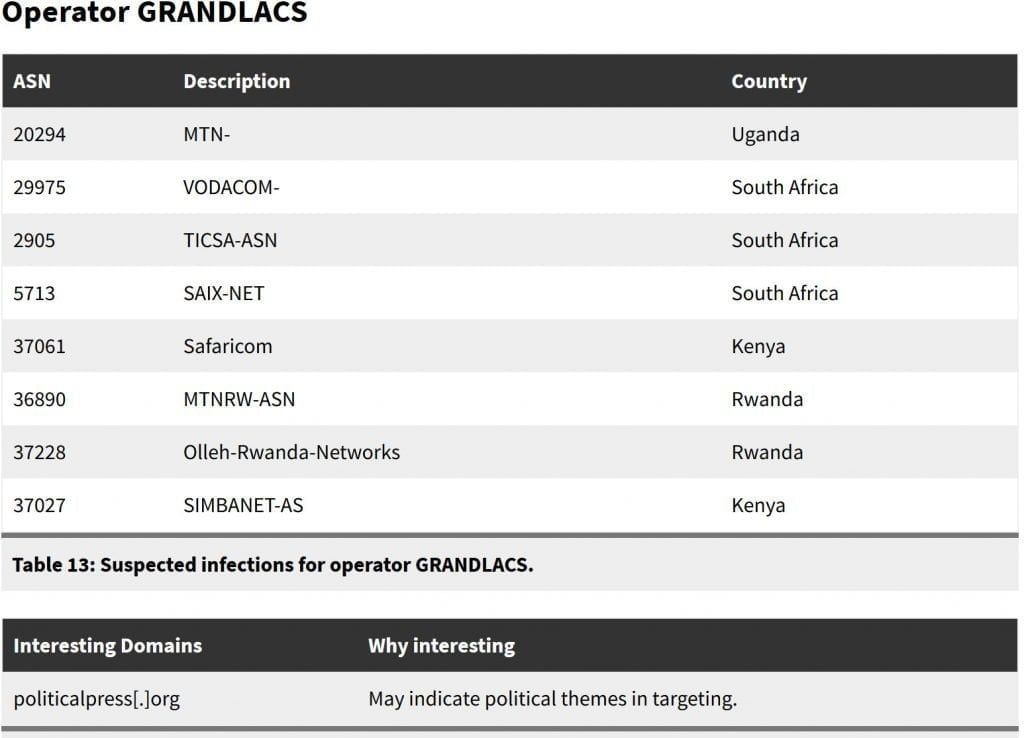
To come up with these findings, NSO used the technique called Athena to cluster the IP addresses that matched their Pegasus fingerprints into what they believe are 36 distinct operators; each operator makes use of multiple IP addresses. They gave each operator an Operator Name drawn from national symbols or geographic features of the country or region that appears to be targeted. For each IP address used by the operator, they extracted a domain name from its TLS certificate. NSO coded the domain names to generate a Suspected Country Focus and assessed whether there were Political Themes in the domains, which might suggest politically motivated targeting. The security company then performed DNS cache probing to generate a list of countries in which there are Possible Infections associated with the network operator.

